Social engineering is a term used for the general practice of manipulating people to perform actions or divulging confidential information they normally would not.
- An attack trying to get you to reveal personal information (e.g., account name/password, Social Security Number, mother’s maiden name) that can be used for identity theft.
- An attack trying to get you to run an executable file of any type in order to load a virus, worm, Trojan, or other malware on your system. (This may result in identity theft ultimately but the primary objective is to get you to load the malware.)
Pretexting
This has nothing to do with phones and text messages. The term comes from an attacker inventing a scenario (or pretext) to persuade a target to give out information or perform an action.
An example from the corporate support world has an attacker posing as someone from the corporate computer support department. They call various managers’ secretaries (who often handle the boss’ E-mail) saying that they need the boss’ log-on information in order to perform some sort of security upgrade or security check (or…whatever – invent your own situation). If the secretary is very busy or has not been properly trained they might give out the information. This then gives the attacker an entry into the corporate network that can be exploited. Part of that exploitation may be to gather even more private information so that calls can then be made to others in the company with the caller sounding even more authentic.
The term social engineering was popularized by reformed computer criminal and security consultant Kevin Mitnick. He pointed out that it’s much easier to trick someone into giving you his or her password for a system than to spend the effort to hack in. He claimed was the single most effective method in his arsenal.
Ramy, Muzher, and Shadde Badir, brothers blind from birth, set up an extensive phone and computer fraud scheme in Israel in the 1990’s using social engineering, voice impersonation and Braille-display computers.
According to Wikipedia![]() other noted social engineers include Frank Abagnale, Dave Buchwald, David Bannon, Peter Foster and Steven Jay Russell.
other noted social engineers include Frank Abagnale, Dave Buchwald, David Bannon, Peter Foster and Steven Jay Russell.
Phishing
Similar to pretexting, phishing is designed to fraudulently obtain private information. Generally, phishing does not involve personal contact however; instead, legitimate looking E-mail, websites, or other electronic means are involved in phishing attacks.
The term phishing is a variant of fishing which might be used to describe the process of “fishing” for information. The “ph” in place of the “f” was probably influenced by phreaking. The word may also be linked to leetspeak![]() , in which “ph” is a common substitution for “f”.
, in which “ph” is a common substitution for “f”.
Phishing messages will typically emulate messages supposed to be coming from a trustworthy site like eBay, PayPal, or an on-line bank. They often indicate something is wrong or needs confirmation and give you links that look, on the surface, like they go to the site in question. In fact, these links send you to a website that is made up to look like the real website (often using all the graphics, links, and styles on the real sites). These sites then ask you to log in. When you do, there will often be an error message of some kind asking you to come back later but by then it’s too late. The phisher has your login information and usually uses it within minutes to log in as you. As you, they can then perhaps change the login information so you can no longer log into the account and they then have full control over your data and perhaps your money and any personal information stored on the site.
As an example, let’s say you got an E-mail that looked like it came from PayPal and had a link in it to update your information. That link may very well take you to a site that is trying to steal your login information and, with it, any money you might have in your PayPal account or in any bank accounts connected to your PayPal account. The link may look OK at a quick glance but might say paypol instead of paypal (an easy spelling error that’s easy to overlook particularly since it’s likely hidden and only shows up when you hover your cursor over the link itself. You can see that this has been done by using Google to search for URLs with paypol in them. One of the results that comes up indicates this has been tried…
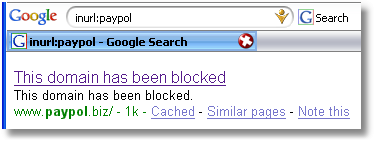
Always type in a domain yourself or use a bookmark you set yourself when attempting to go to a site that contains any personal information about you. Never trust a link in an E-mail of questionable origin no matter how good it looks. As but one consideration, a valid E-mail from any site where you have an account will generally have some personal information it the messages itself (e.g., Dear [your name]). If the message simply says “Dear PayPal Customer” then immediately suspect it.
Phishing has been around for some time. The first recorded mention of the term is on the alt.online-service.America-online Usenet newsgroup on January 2, 1996. The term may have appeared earlier in the print edition of the hacker magazine 2600. A phishing technique was described in detail as early as 1987, in a paper and presentation delivered to the International HP Users Group, Interex.
Phishing started in earnest by capturing AOL account information in order to steal the credit card information from the accounts. This lead to attempted attacks directly targeting electronic payments systems. The attacks expanded after 11 September 2001 when ID checks became popular. By 2004 the attacks had become very sophisticated and have increased in number since then. Even the Internal Revenue Service has been a phishing message target.
Once someone has a bit of your information they can then target you specifically, perhaps by name. This makes the phishing attack seem much more real and you have to be that much more careful. Such targeted attacks are often called “spear phishing.”
Social networking sites like MySpace are also coming under attack as they often contain personal data that can be used for other purposes. There are reports that experiments targeting social network sites succeed over 70% of the time.
These techniques (not a complete list) are can be used in phishing attacks…
- Link manipulation. Described above, this technique basically shows what looks like a valid URL in the phishing message but actually links to the phisher’s site which is made to look like the real site. Some browsers and E-mail programs will warn you before taking you to the link but do not depend on that.
- Filter evasion. Filters can be set up to identify suspicious text. Sometimes images of text are used instead of the text itself in order to get by the filters.
- Website forgery. Javascript can be used to alter the browser’s address bar so that a false site can look like the real site in the address bar. Usually there is a flicker when this happens but it may not always be noticed. It’s better to browse with Javascript turned off (a good solution seems to be to use a browser like Firefox with the NoScript add-on extension; the extension prevents scripts from running on sites you have not approved in advance). More sophisticated attacks are also possible in this regard where the actual scripts on the real site may be used against it if those scripts have flaws in them. Flash is also sometimes used to hide text in a multimedia object.
- Phone phishing. While phishing is normally done via E-mail direction to a website, phone messages can be used to have users dial an institution’s phone number which is actually controlled by the phisher. Fake caller-ID information can make these attacks seem very real.
What can you do to protect yourself against phishing?
- Educate yourself.
- Modify your browsing habits. In particular, if contacted by anyone who says you need to verify an account or log-in to do something specific be certain to know why the message was sent. If you are not expecting the message contact the company involved directly (don’t use any of the links in the message; go directly to their website by typing it into the browser address bar). (Note: While still the best way to get to an important website, keep in mind that if your computer has been infected with malware that has changed the HOSTS file
 [the file Windows keeps locally to match domain names and IP addresses] then it’s still possible you will be taken to a fake website. Rare, but possible.)
[the file Windows keeps locally to match domain names and IP addresses] then it’s still possible you will be taken to a fake website. Rare, but possible.) - E-mail coming from a company you will have an account with generally will have personal information in it and not be addressed to “Dear [Company] customer” or the like. Again, not foolproof (see spear phishing above) but one indicator.
- Use all the technical measures available to you…
- Many modern browsers will sometimes issue a warning when a site shows evidence of being a phishing site or the site URL is in a database of phishing sites kept by the browser maker and checked when a Web page is accessed.
- Browser add-ons can be found that display the actual URL of the website visited even if Javascript on the page tries to fake the address bar.
- Watch images carefully. If they are improperly served from a legitimate site to a phisher’s site it’s possible the images will be modified to say that.
- For banks, take advantage of all augmentation you can find instead of just using a log-on/password combination. Some banks now ask you to specify a specific image when you create an account and then show you that image when you execute a proper log-in. A phisher’s site won’t have that picture. Not an absolute protection but if it’s available use it and pay attention to it. Other banks may give you a secure key that changes every 30 seconds or so and you are required to enter the number from the key when logging into a legitimate site.
- Report any phishing attempts you may encounter to the bank or other site involved. They will likely attempt to take the site down.
There are several laws that have been enacted to help stop phishing and phishers but, in the end, it’s up to you to use proper care.
You can keep track of phishing attacks at the Anti-Phishing Working Group![]() website
website
Some Examples
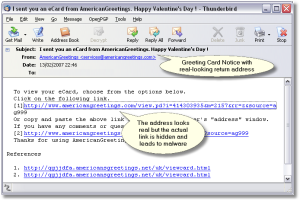
Often holidays will lead to social engineering attempts. Valentine’s Day is a popular one as shown here from 2007…
While the message appears real, if you click on the link are are taken to a page which tells you that you need a new Flash player and gives you a download link. The file coming from this link usually contains some form of Trojan or other malware that installs itself. You may or may not ever see the greeting but be certain that you have been suckered into running something you should not have.
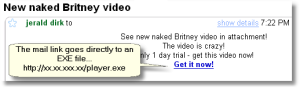
Similar messages are more direct. Take this E-mail message as an example…
You can bet that this sort of come-on will capture some while the player.exe file captures them.
Here’s another that claims to be from the IRS…
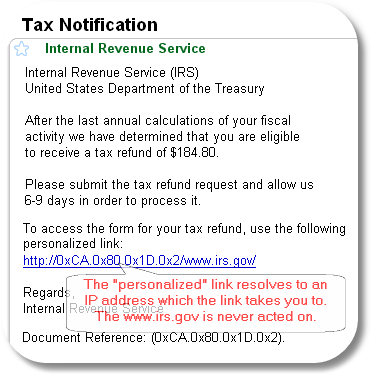
Who doesn’t want a refund? Except, when you click on the link you are taken to the IP address that the URL-encoded characters resolve to and everything after the / following that (the www.irs.gov/ part) is ignored. You can bet there will be a page at the IP address asking for a bunch of personal information in order to “make certain we have the right person” or words to that effect. And, the IRS never sends notices like this which should be the very first clue this is bogus.
And, finally, Social engineering doesn’t always have to be related to stealing identity, it can be about stealing money. Take the following query that might come in via E-mail…
What’s the scam? Since these messages were spammed to many webmasters the most likely scam is a variation on the Advance fee fraud. In this fraud, you agree to sell space for some amount. You get a check for more than that amount and, of course, deposit it. Shortly afterward, you get a message about the error and are asked to wire the difference which, being honest, you do. The wire transfer can’t be reversed once started and a week or more later you find out that the check is not good. So, you’ve given someone a bit of free advertising and some of your money while they sit back and laugh.
None of these things are easy. Science Daily,![]() for example, reports on a study of how easy it is to fool many users with such tactics. It seems it’s not very hard unless the user concentrates and takes note of small things that may be out of place.
for example, reports on a study of how easy it is to fool many users with such tactics. It seems it’s not very hard unless the user concentrates and takes note of small things that may be out of place.
[Added 16 February 2010] – There is a particularly bad scheme going around now. Fake anti-malware software use the technique of a scan that identifies various malware on your system and then ask you to buy the product to remove the malware that really doesn’t exist. When that happens, more is found and the cycle repeats. It’s a common technique for such things. The twist recently added is a support button in the product that lets you chat with a person about the supposed malware found. The chat is reported![]() to be with an actual person and, of course, that person will both add credibility and perhaps be more effective at getting your money. Quite clever actually but the technique ratchets social engineering up a notch as a way to scam you.
to be with an actual person and, of course, that person will both add credibility and perhaps be more effective at getting your money. Quite clever actually but the technique ratchets social engineering up a notch as a way to scam you.
[Added 16 March 2010] – Came upon a site named “contagio![]() ” which posts the latest malware threats and, maybe more importantly, has information about the messages that the malware was sent in. If nothing else, as social engineering is a fast moving target, this collection will give you more examples of the type of thing to watch out for.
” which posts the latest malware threats and, maybe more importantly, has information about the messages that the malware was sent in. If nothing else, as social engineering is a fast moving target, this collection will give you more examples of the type of thing to watch out for.
[Added 18 March 2013] – You can make it easier for social engineers to attack you by sharing way too much personal information on-line. See this YouTube video as but one example of this…it’s magic.
[Added 19 August 2018] – Interesting related post: Identity Theft 101: How it Happens & What to Do if It Does![]()
Summary
- Social engineering is a general term for getting people to reveal or do things they should not.
- There are many tricks.
- Pretending to be someone who should be trusted is one.
- Phishing is another and quite common.
- Social engineering can be used to collect information for actions like identity theft or make people run Trojans to infect their systems and maybe set them up into a botnet.
| Botnet | Peer-to-Peer Network |
Comments from original post:
Jeremy Flit
Said this on 2010-02-10 At 05:20 pm
Loved your article. Found another one that talks a bit about what is going on this week with SE attempts related to valentines day: http://www.jocktoday.com/2010/02/08/social-engineering-and-valentines-day/