Peer-to-peer networks connect multiple computers together but you really don’t know who your computer might connect with and this introduces the potential for mischief.
One of the earliest P2P network, and one still operating, is the Usenet news server system. In that system peers connect to distribute Usenet news postings which eventually cover the entire network, stored on distributed news servers which collected and archived new messages as they came across the system. Some of these postings were or contained binary data, some infected. These were purged from the system when found but managed to find their way onto individual systems none-the-less.
Some P2P networks today use a hybrid network form. Napster, Open NAP, and IRC, for example, use a client-server approach for tasks like searching for files or sections of files to share and a peer-to-peer approach for the actual file sharing. Gnutella and Freenet (to name but two) use P2P techniques for everything.
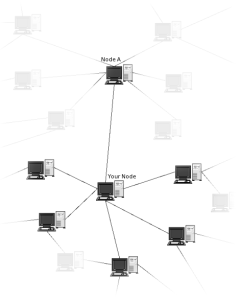
One of the fairly obvious concerns with P2P systems is that in order to participate in one the user has to run client software on their system that actually puts their computer into the network with everyone else who might be a part of the network. Generally, all the other computers in the network are unknown to other computers on the network so you never know what you are connecting into. This diagram shows a typical Freenet connection where only the computers directly attached can be seen; the others are invisible to the connected user…
Since P2P systems are often attacked there are some possible problems that come with that connection…
- Files coming across the network with content different than the description that comes with the file; called a poisoning attack. Basically, you never really know if you are getting what you think you are getting.
- Pollution of the files on the network by the addition of bad digital material to the file making it no longer a valid file.
- Members of the network who only download files but do not allow their computers to host material for others to download (Freeloaders or Leechers). This makes it necessary for the remaining computers on the network to work a bit harder which steals resources from them.
- Insertion of viruses or other malware into the files being carried on the network. Viruses can be anywhere so if an infected machine connects to a P2P network it’s well within the realm of possibility that the infected machine will be able to attach the infection to the data stream and thus infect other computers on the network when the complete file is run or opened.
- Malware may exist in the peer-to-peer client software needed to connect to the network itself. While usually not a virus this may be adware or spyware that could be quite difficult to remove once it’s installed itself.
- If the network itself is attacked with a denial of service attack in order to make it run slowly or fail then computers in the network will be made part of that attack with unpredictable results.
- Spamming of unsolicited material can take place across P2P networks either directly or as part of a denial of service attack.
- Since many P2P networks contain illegal material to download (movies, songs, software, etc.) it’s quite possible that as a member of such a network your identity on the network alone will make you a target of legal actions against the network because of the content; even if you are not using the network in any illegal manner. This can cause personal problems up to and including the necessity of hiring an attorney to defend yourself for doing nothing wrong (assuming you did nothing wrong) :-).
This is not to say that all P2P networks are bad or even vulnerable. Most attacks can be controlled or even defeated through careful design. But, no matter what, if the majority of other computers on a P2P network are somehow infected in a way that affects the network no amount of design is going to overcome the problems; and, it may not even take that many.
As but one example, on 25 January 2009, Intego reported that OSX.Trojan.iServices.B Trojan Horse, “…is found in pirated software distributed via BitTorrent trackers and other sites containing links to pirated software. OSX.Trojan.iServices.B Trojan horse is found bundled with copies of Adobe Photoshop CS4 for Mac. The actual Photoshop installer is clean, but the Trojan horse is found in a crack application that serializes the program.”
Summary
- File sharing software used to connect to a peer-to-peer network may contain malware; particularly spyware or adware that can be difficult to remove once installed.
- Such software affects computer performance.
- The malware may compromise a user’s identity by capturing keystrokes used to log into sites and sending these across the network to others waiting to misuse them.
- Files may not be what they seem. A movie could possibly suddenly turn into a pornography either entirely or part way through.
- While connected to a P2P network your computer is possibly vulnerable to any general attacks on the network itself.
| Social Engineering | Search Poisoning |
Comments from original post:
Kiber
Said this on 2010-01-15 At 05:01 am
please sample project proposal of per to per Network installation and configuration document.
#2
DaBoss
Said this on 2010-01-15 At 12:50 pm
In reply to #1
Sorry. Too many variables to do that. You’ll have to do your own homework.
#3
olsi
Said this on 2010-06-02 At 03:18 am
thank ypou for your help
#4
Sheikh Nayyer Raza
Said this on 2010-07-31 At 05:08 pm
How many computers we can attach in peer to peer network?
Is peer-to-peer communication a better choice when number of nodes is increasing largely? Explain
#5
DaBoss
Said this on 2010-07-31 At 05:16 pm
In reply to #4
In general you can have as many as you want but the network will likely slow down some as you add computers to it. If you need more a Google search brings up a large number of peer-to-peer information pages. Microsoft has a good one here…
http://technet.microsoft.com/en-us/library/bb457079.aspx